
How to Strengthen Your Cybersecurity via Artificial Intelligence
Technology has grown to significant heights in the past few decades. The steeping advancements have made possible all the things that were unimaginable quite some time back.
We are living in a world of technology, digitalism, and modernization. These advancements have enabled the use of robotic and artificial intelligence in our life.
The example of this rapid acceptance and practice can be taken from the following as there is a 270% increase in artificial intelligence in the organizations in the past four years.
It has been estimated that by 2022, 80% of the emerging technologies will have Artificial intelligence foundations.
With the increasing use of technology, the risks of cybersecurity and data breaches increased massively. But, with the advent of artificial intelligence and machine learning, cloud security and cybersecurity are strengthening.
Cyber Attacks can be Horrendous!
Cyber-attacks are dangerous and can seriously lead to unpleasant circumstances. Cyber-attacks can be troublesome in the following ways;
- The invasion of privacy through different web browsers.
- Cyber-attacks such as phishing, spoofing, and spamming.
- Injecting viruses in the systems.
- Password breaches.
- Vital information or data can be sabotaged.
- Hacking of personal or business accounts.
- Impersonation of different platforms.
- Blackmailing through stealing the crucial information.
- Intellectual property can be manipulated.
- Money scams.
- Ransom and malware attacks
But, all these mainstream cybercrimes can be avoided with steps such as strengthening your cybersecurity with artificial intelligence.
Artificial Intelligence for Cybersecurity
Cybersecurity has proven to be a massive threat as more breaches and data thefts happening every other day. According to Fintech News, every 39 seconds, there is a cyber-attack, and approximately 75% of cyberattacks start with a simple email.
Billions of people are connected digitally, and the world is spending more on cybersecurity to strengthen it. According to Statista, worldwide spending on cybersecurity is expected to reach $43 billion by 2022. With the growing complexity of cyber-attacks, artificial intelligence helps security operations stay ahead and align with the increasing threats.
AI has advanced in providing instant and accurate insights to help you fight through the tons of threat alerts, reducing the response time drastically. Artificial intelligence-led technologies like machine learning and natural processing language enable the analyst to respond to threats with great efficiency, reliability, and speed.
AI technology is learned by consuming and viewing billions of data to reason and present the first-hand solutions, which are excellent and efficient in strengthening cybersecurity.
Artificial Intelligence Applications for Strengthening Cybersecurity
Artificial intelligence is strengthening cybersecurity as complex problems require complex solutions.
1.Automation in Network Analysis
A significant amount of cyber-attacks and malware occur on computer networks. In this regard, any attempt to install the malware and command-and-control (C2) communication to pursue intrusion can be monitored with network communications.
Malware creators find it very easy to merge with the open traffic on the network by exploiting the C2 protocols. They place malicious data in the HTTP header that easily breaches the firewall by embedding with DNS requests.
AI technology and ML have need-based algorithms which are used as a technique to match the keywords, provide efficient monitoring on the statistics, and detect the anomaly to identify the data packers (outbound or inbound).
2. Machine Learning for Anti-Malware
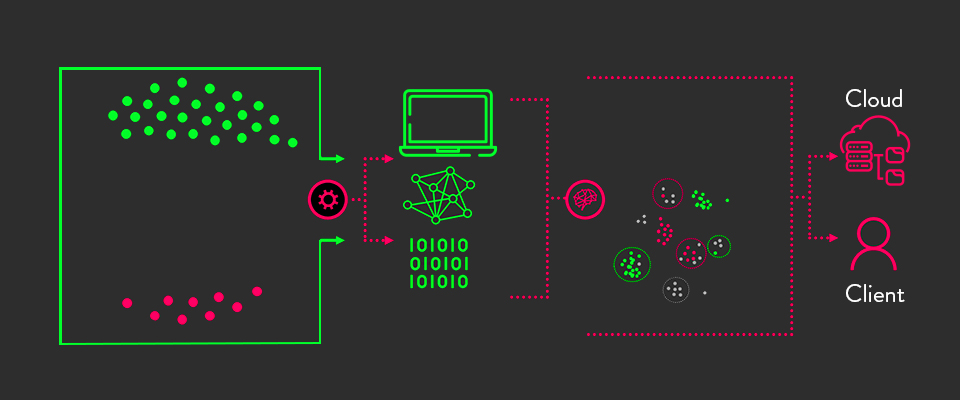
The computers, devices, gadgets, and other systems are increasing magnificently. With this increase, the possibility of catching the virus and being under siege is entirely possible. Malware creators are always on the look to find the loop and invade.
Artificial intelligence has been advanced with developing antivirus programs that can detect unusual software behavior to track and identify the potential presence.
An example of this AI-based antivirus program to detect the malware and potential virus is Microsoft Windows Defender. This program is mainly designed and created to monitor the system performance and flag the unusual activity. Network Intrusion (Detect & Prevent)
3. Network Intrusion (Detect & Prevent)
Network intrusion happens most of the time. The unauthorized activity on a digital network, in which intrusions and stealing of valuable data and network resources jeopardized the attacked-party.
Various factors can source network intrusion. Examples include multi-routing, buffer overwriting, multi-connectivity, CGI (Common Gateway Interface) Scripts, flooding of traffic, protocol-centric attacks, Trojan Horse Malware, and Worms. These are some of the factors that can lead to network intrusion.
But it can detect and prevent if timely actions are taken with significant consideration and active responses, by,
- Installation of rootkits.
- Using high-end encryption of the other-end data.
- Deleting logs.
- Set a routine of tracking the behavioral changes on a daily or monthly basis.
- Regular configurations, tuning, and maintenance are of high demand.
- The use of AI technologies would help in the prevention of network breaches.
4. Security of User Authentication
User authentication secures the process of human-to-computer interaction by asking to insert a login ID and a passcode.
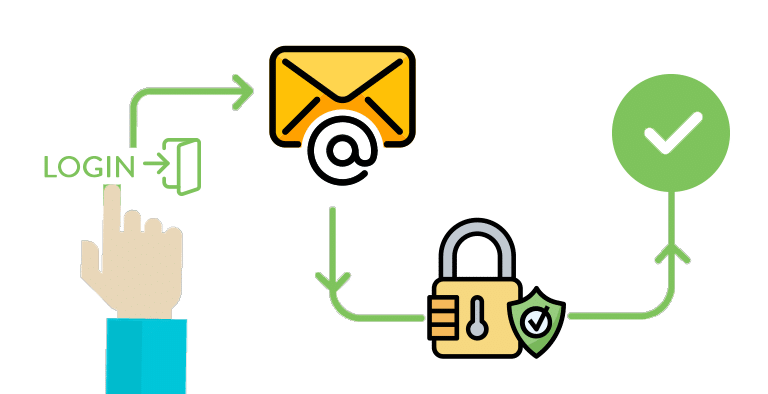
User authentication has three main tasks;
- The first is to manage the connection between the human and the website’s server.
- The second step is to verify the login ID and passcode.
- The third step is to approve the authentication of the person requesting to enter by authorizing the user.
There are many ways to strengthen user authentication with and without AI-based programs, such as by supporting the passcodes or setting up a two-way authentication code.

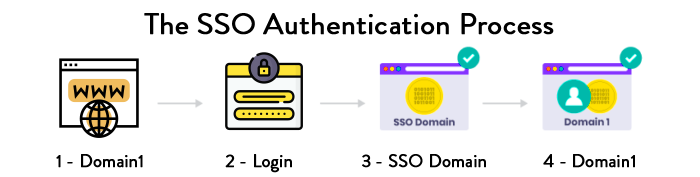
SSO (single sign-on) authentication is another probable and result-oriented way to save from the cyber-attack and ensure cybersecurity.
5. Botnet Detection
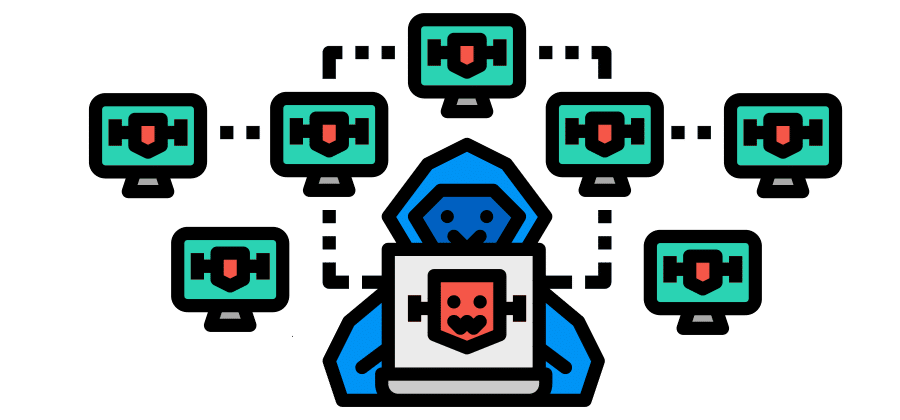
Hackers can control the botnet. They track the malware and nature of the cyber-attack. Cybercriminals use botnets to track malicious activities such as credentials leaks, authorized access, and data thefts. The process of attack with a botnet is called DDoS (Distributed Denial-of-Service).
With the increasing cyber threats, the detection and prevention of botnets are important. After several types of research on botnet detection and analysis, it was found that detecting botnet activity can be done by classifying network behavior with the advanced use of machine learning.
Fraud Detection
Fraud detection is the most happening thing in cybersecurity. Fraud detection can easily be detected with the effective deployment of machine learning tools and models.
For example, the dataset is the ML-based technology that can track the credit card transactions to train the model to recognize fraud. This technology is developed to enhance and learn itself with which it can adopt new ways to counter the new and uprising fraud patterns.
Hacking Forecasting
ML can forecast hacking intentions. ML-based algorithms work and collect the facts and information about forecasting incidents.
ML-based programs help forecast the hacking, such as the defenders, Bayesian method, ARIMA, and FARIMA models.
Benefits of Using AI in Cybersecurity
The benefits of AI in cybersecurity have been discussed below;
IT Inventory
AI helps cybersecurity in IT asset inventory by gaining an accurate and complete list of all the running devices. This has been implemented in big organizations.
Effective Control
Various security tools require constant monitoring and processes. By using AI in cybersecurity, you can get effective control over the systems. For instance, essay writing service providers are highly vulnerable to data breaches, so implementing AI would give you an edge in controlling.
Breach Prediction
With AI-based programs in action and with the IT asset inventory, AI predicts what is most likely to be breached and helps you secure the platform.
Active Response
AL programs help in providing the improved context for prioritization and security alerts for rapid responses.
It is essential for writing agencies of different sizes to view and reply to all queries, e.g., students seeking student essays can bring malware to your network. But, with AI in action, it can be monitored, tracked, and eliminated.
Conclusion
AI has been changing the world dynamics in plenty of ways. With the increasing adoption and reliance on technology and devices, the chances of threats increase more than ever. AI strengthens you to counter the cyber-attacks and be safe at the same time.
Author Bio
Claudia Jeffrey is working as Content Strategist & eCommerce Manager at Dissertation Assistance, a splendid platform that provides dissertation help. She has been working with leading minds and has a great interest in producing superior technology and digital content for her audience.
Recent Blogs
- The Gig Renaissance: Why Smart Businesses Hire Remote React Native Developers on Contract
- Hire Remote Golang Developers: Powering Cloud-Native and Microservices Growth
- Hire Best Remote Software Developers: Why AI Can’t Replace Human Expertise
- Low-Code RPA: Empowering Citizen Developers Through Automation
- RPA Software Solution: Intelligent Document Processing with RPA
Categories
- Agritech (1)
- AR/VR (5)
- Artificial Intelligence (55)
- Machine Learning (1)
- Blockchain (4)
- Business Intelligence (3)
- CRM (5)
- SalesForce (4)
- Data Engineering (8)
- Data protection (2)
- Development (103)
- Golang Development (16)
- Python Web Development (9)
- React JS (5)
- React native (10)
- Devops (3)
- Hire Developers (4)
- Internet of Things (IoT) (5)
- Kubernetes (2)
- Machine Learning (2)
- Mobile App Development (44)
- Node.js (7)
- outsourcing (7)
- Partnership (4)
- Performance Testing (3)
- RPA (24)
- Security (24)
- Strategy (1)
- Testing (110)
- Accessibility Testing (2)
- Automation Testing (22)
- Dynamic Testing (1)
- Manual Testing (3)
- Mobile App Testing (13)
- Offshore Software Testing (6)
- Penetration Testing Services (13)
- QA testing (16)
- Remote Software Testing (7)
- Software Testing (19)
- Website Design (22)